Enabling SSL for FlowForce Web Server
The instructions below show you how to enable SSL for the "FlowForce Web Server" service, that is, the service which drives the Web administration interface of FlowForce.
Prerequisites:
•You need a private key and its corresponding certificate signed by a certificate authority trusted by your browser (such as DigiCert, Comodo, and so on). You also need all the intermediary certificates provided by the certificate authority. For information about obtaining these, see Signing SSL Certificates with a Certificate Authority or Creating Self-Signed SSL Certificates.
•Both the certificate file and the private key must be in PEM (Privacy Enhanced Mail) format. The file extension of PEM files is usually .pem but it can also be .key, .cert, .cer, or .crt.
•The certificate must be issued for the domain name on which FlowForce Server is running.
•The private key of the certificate must not be encrypted with a password, see Private Key Requirements.
•If you created self-signed certificates, each client browser must be configured to trust your self-signed certificate authority, see Importing Root Certificates.
Once the prerequisites are met, you can secure the connection between a browser and FlowForce Web Server as follows:
1.Open the FlowForce Server setup page.
2.Find the settings grouped under "FlowForce Web Server" and do the following:
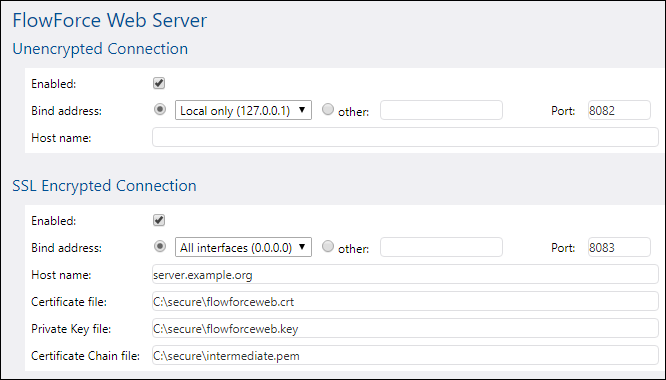
a.Select the Enabled check box under "SSL Encrypted Connection".
b.Next to "Bind address", select All interfaces (0.0.0.0) (assuming that FlowForce Web Server should be accessible from the outside world, not just locally from the current machine).
c.Enter the host (domain) name and port where FlowForce Web Server should listen for SSL encrypted connections, in the Host name and Port fields, respectively.
The domain name entered in the Host name field must correspond to the SSL certificate's Common Name. The port must not be in use. |
Depending on the case, you can also select "other" and enter the IP address where FlowForce Server listens for SSL encrypted connections. If you entered an IP address in the "other" field without entering a host name, this IP address must correspond to the SSL certificate's Common Name.
d.Enter the path to the certificate and private key file in their respective text boxes.
Note •The certificate must be in PEM (Privacy Enhanced Mail) format. The file extension of PEM files is usually .pem but it can also be .key, .cert, .cer, or .crt. •The private key must be in PEM (Privacy Enhanced Mail) format. The file extension of PEM files is usually .pem but it can also be .key, .cert, .cer, or .crt. •In order for the private key to be usable in FlowForce, it must not be password protected, see Private Key Requirements. •The private key must be stored securely. |
e.Enter the path to the certificate chain file in the Certificate Chain File field. If there is no intermediary certificate, then you can leave this field empty. If there are several intermediary certificates available, then you must combine all of them into a so-called "Chain File" which contains all the intermediary certificates, as described in Preparing Intermediary Certificates.
f.Optionally, clear the Enabled check box under "Unencrypted Connection". Note that this will make FlowForce Web Server unavailable through plain HTTP, so you should take this step only after the SSL encrypted connection works. Instead of disabling the HTTP connection completely, you may want to restrict it to local connections only, as shown in the image below.
3.Click Apply settings and restart FlowForce services.
After you select the SSL Enabled check box and click Apply settings and restart FlowForce services, the browser will be redirected to the "https" (not the "http") URL. |
Note the following:
•The browser (or connecting client) will still display warnings if the Common Name (CN) of the SSL certificate does not correspond to the domain name or IP address where FlowForce Server runs.
•If you are using self-signed certificates, the browser (or connecting client) will still display warnings if you did not add your CA root certificate to the operating system's certificate store, or to the browser's certificate store (see Importing Root Certificates)