MobileTogether Server is the back-end hub for your enterprise solutions and app store apps built using MobileTogether Designer. It acts as a gateway between end-users and your back-end data sources and infrastructure. In addition to numerous high-performance app hosting features, MobileTogether Server supports definition of a variety of granular security options, both on a per-server basis and a per-app basis.
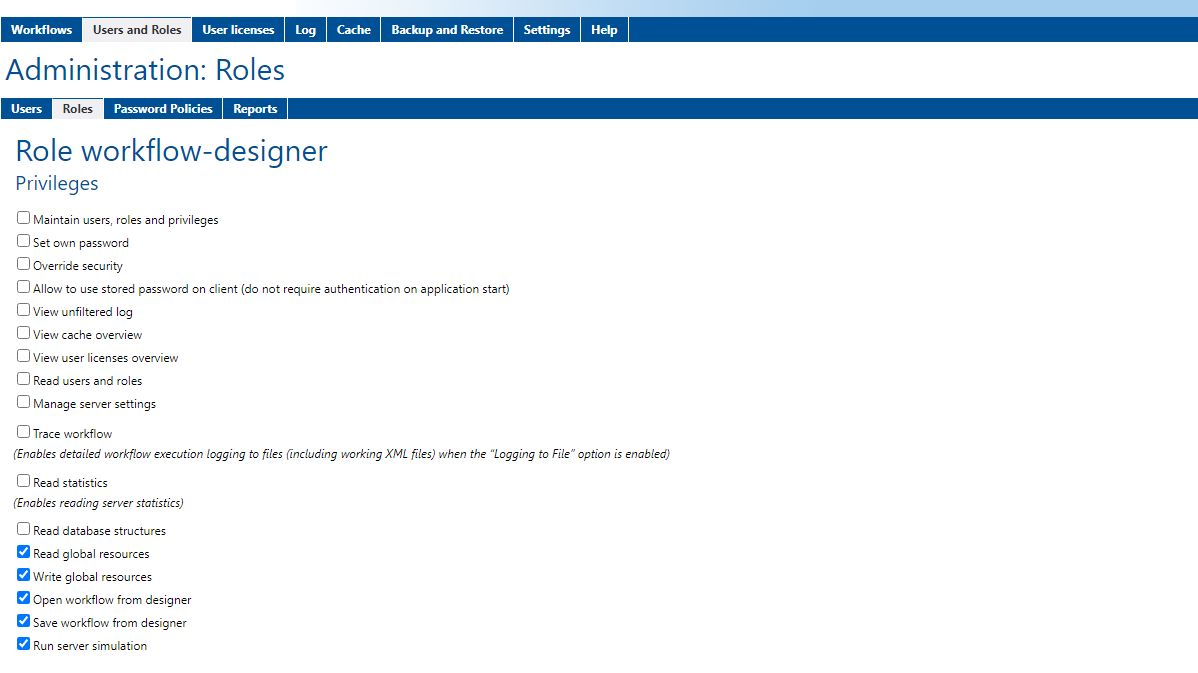
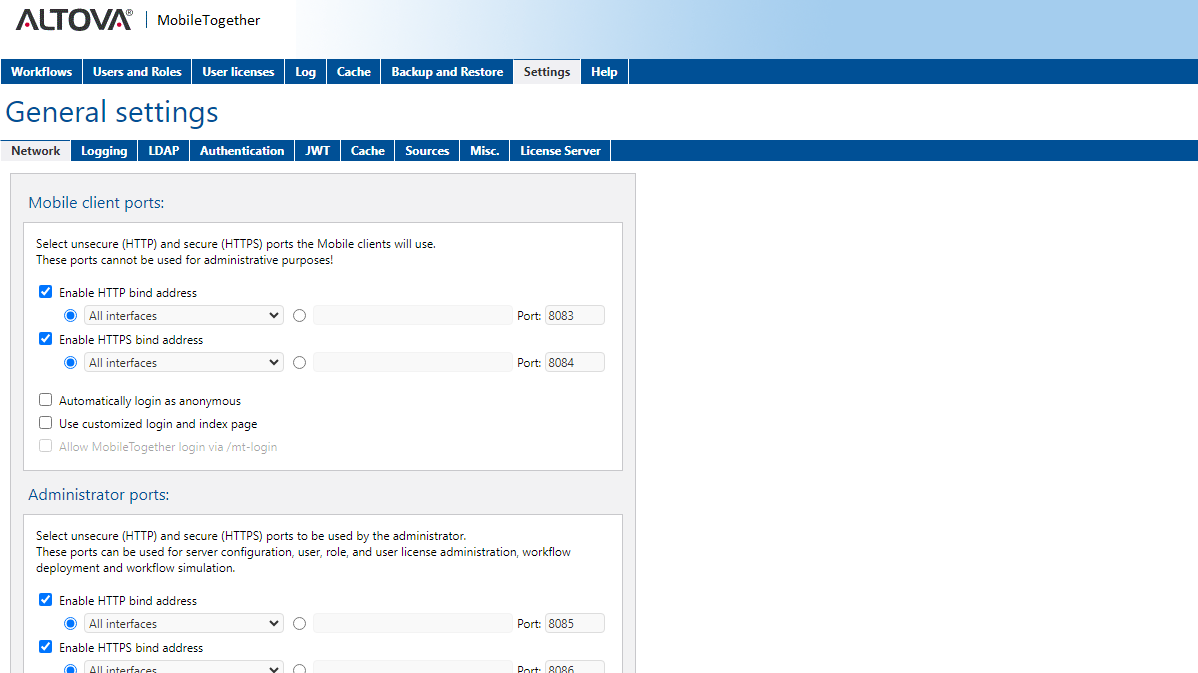
An easy-to-use web interface and permissions editor makes it easy to enable and manage roles, authentication, and encryption.