Directory Service
If your organization uses Microsoft Active Directory or an LDAP-compliant directory service provider such as Apache Active Directory, OpenLDAP Server, Oracle Unified Directory, and others, you can integrate it with FlowForce Server. From the FlowForce Server perspective, integration with a Directory Service provider means the following:
•Users can log on to FlowForce Server with their domain user name and password.
•Administrators can either allow existing domain users to log on to FlowForce Server with their domain credentials (that is, an implicit user import takes place), or they can explicitly import domain users and groups into FlowForce Server. In either case, the imported accounts are visible in the user administration pages of FlowForce Server. This enables administrators to add or revoke privileges and permissions to groups or user accounts, in the same way as for the built-in FlowForce Server accounts (see About Privileges and How Permissions Work). Administrators can also assign FlowForce Server roles to groups or user accounts (see Assign Roles to Users).
•Administrators cannot rename or change the password of domain users imported into FlowForce Server.
•Administrators cannot rename or change the membership of domain groups imported into FlowForce Server.
•Administrators can delete imported domain accounts from FlowForce Server. This does not remove the accounts from the domain and does not change in any way their associated domain privileges.
•If the imported domain accounts have FlowForce Server privileges and permissions assigned to them, they are displayed in privilege reports (see Reports).
To change the Directory Service settings:
1.Log on to the FlowForce Web administration interface.
2.Go to the Administration menu and click Settings.
The available settings are described below.
Enable
Select this check box to enable users to log on to FlowForce Server with their domain user name and password. If you select this check box, you must select either the Active Directory or the Lightweight Directory Access Protocol (LDAP) option, as further described below.
If you select the Lightweight Directory Access Protocol (LDAP) option, make sure that connection details (such as username, password, and so on) are correct. When you click Save, FlowForce attempts to communicate with the specified LDAP server and shows an error if it the connection details are not valid. Note that FlowForce Server must be able to connect to the LDAP server successfully before you can save the LDAP settings.
If you select the Active Directory option, the machine where FlowForce Server runs must be part of a domain controlled by Active Directory.
After you have enabled directory service authentication, an additional drop-down list becomes visible in the FlowForce Server login page, called Login. The Login drop-down list enables users to select the authentication option and contains the following items:
•Directly. This is the default FlowForce Server authentication option. To log in, users must supply their FlowForce username and password.
•[A specific domain], depending on the configured LDAP server. To log in, users must supply their domain username and password—these are managed by the LDAP server.
See also Logging on to FlowForce Server.
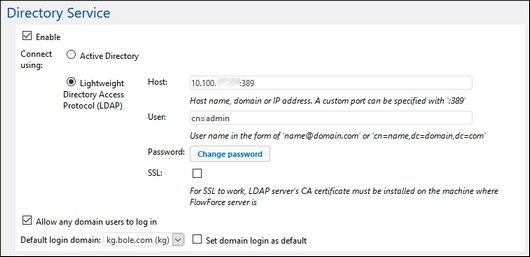
Connect using
Select Active Directory to enable direct integration with Active Directory. This is applicable if FlowForce Server runs on Windows and the machine is part of a domain controlled by Active Directory.
Select Lightweight Directory Access Protocol (LDAP) to enable integration with an LDAP-compliant Directory Service. Fill in the details as follows:
•Host — Enter the host name, domain name, or IP address of the LDAP server. To add a port number, append a colon character, followed by the port number. For example, somehost:10389
•User — Enter a user name which has administrative rights to query the directory service. The user name can either be in the form of a "Distinguished-Name" (for example cn=name,dc=domain,dc=com) or a "User-Principal-Name" (for example, user@some.domain.com). Note: The "User-Principal-Name" format applies for Active Directory only; for other LDAP servers, use the "Distinguished-Name" format.
•Password — The user's password. Note: If you mistype the password several times, the LDAP server may lock the account. In that case, make sure that the account is not locked out before proceeding.
•Use SSL — Select this check box only if the LDAP server was configured to accept SSL-encrypted connections from clients. If you select this option, change the port number to the one used by the LDAP server for secure connections (typically, port 636). If your organization already uses the same trusted root certificate on both machines, there are typically no additional configuration instructions. Otherwise, the root (CA) certificate of the LDAP server must be installed on the machine where FlowForce Server runs, as follows:
a.On the machine where LDAP server is, export the root certificate from the trusted certificate store. Use the tools specific to your operating system for that purpose (for example, the Certificates Snap-In on Windows).
b.On the machine where FlowForce Server is, import the certificate into the trusted certificate store, as described in Import Root Certificates.
Note: On Windows, SSL errors are reported in Windows Event Viewer | Windows Logs | System, where Source is set to Schannel.
In some cases, LDAP servers can have arbitrary schemas that do not fit into a particular standard. If FlowForce Server cannot detect the schema of your LDAP provider, an error similar to "Directory Service detected an invalid LDAP schema" is displayed. In this case, copy the directoryservice.cfg file to the same directory as the FlowForce Server executable. When this file is present, FlowForce Server will not attempt to detect the schema of the LDAP provider automatically.
Allow any domain users to log in
Select this check box if a user's domain account should be imported into the FlowForce user database first time when users log on to FlowForce with their domain credentials. If this option is disabled, domain users can log on to FlowForce Server only if their account has already been imported into FlowForce Server by an administrator.
Default login domain
This option is visible after the Enable check box is selected and the settings have been saved.
The drop-down list displays all domains that this machine is member of. The same list of domains will be visible to users in the FlowForce login page, if Directory Service authentication is enabled (see the first option above).
Select the Set domain login as default check box if the domain should be selected as the default choice in the Login drop-down list of the FlowForce Server authentication page.
If you clear the Set domain login as default check box, the built-in FlowForce Server authentication ("Directly") is the default choice.