Create Self-Signed SSL Certificates
This demo shows you how to create self-signed SSL certificates for FlowForce Server running on a private network. Note that this demo is intentionally simplified and not suitable for use in production. Your organization will likely have specific security policies concerning SSL certificates and could use SSL tools other than the ones described below.
Creating self-signed SSL certificates involves the following procedures:
1.Creating a root certificate
2.Creating a FlowForce certificate
3.Importing the root certificate
For more information about each step, see the subsections below.
Prerequisites
This example makes use of the OpenSSL toolkit (https://www.openssl.org/) to generate self-signed certificates. Note that OpenSSL is an open source library and may need to be compiled before you can use it at the command line. The compilation and installation instructions for OpenSSL vary for each operating system. OpenSSL typically comes pre-installed on most Linux distributions and on macOS machines. You can quickly check if OpenSSL is installed by typing the command below (it displays the current OpenSSL version):
openssl version
OpenSSL can also be installed on Windows computers. For download links to installer binaries, see the OpenSSL Wiki.
Step 1: Create root certificate
The instructions below explain how to create a root certificate. The root certificate will be used to sign the server certificate (Step 2 below).
1.Create a directory that will store all certificates used in this demo (e.g., C:\secure). This will be the working directory for all subsequent OpenSSL commands. Then change to this directory from the command line:
cd C:\secure
2.For this demo, we will be issuing certificates with OpenSSL extensions. To make this possible, find the openssl.cnf file of your OpenSSL distribution and copy it to the working directory created in the previous step.
3.Create the root key that acts as your certificate authority's (CA) private key. Be aware that the root private key is the most sensible piece of your public key infrastructure, so it must always be generated and stored in a secure environment (in this demo, it is stored in C:\secure).
openssl genrsa -aes256 -out root.key 2048
When prompted, type a password to protect the root key. You will subsequently need this password to sign certificate requests.
4.Create the root certificate that is the public certificate of your certificate authority. The command below generates a self-signed certificate for the private key created above, with a validity of 3650 days. Notice that the -config parameter points to the openssl.cnf file in the same directory. The -extensions parameter refers to the v3_ca extension (section) defined in openssl.cnf.
openssl req -config openssl.cnf -extensions v3_ca -x509 -new -nodes -key root.key -sha256 -days 3650 -out root.pem
When prompted, enter information about your organization, for example:
Country Name (2 letter code) [AU]: AT
State or Province Name (full name) [Some-State]: .
Locality Name (eg, city) []: Vienna
Organization Name (eg, company) [Internet Widgits Pty Ltd]: MyCompany Ltd
Organizational Unit Name (eg, section) []: IT
Common Name (eg, YOUR name) []: Demo CA
Email Address []: test@example.org
You can fill in the required fields as applicable to your organization. For the Common Name field, enter the name of your self-signed certificate authority (Demo CA in this example).
Step 2: Create FlowForce certificate
The next step is to create the actual certificate that will be used for SSL encryption (by FlowForce Server, FlowForce Web Server, or both). The FlowForce certificate will be signed with the root certificate that was created in Step 1.4. Follow the instructions below:
1.Create the private key, using the OpenSSL command below. The private key accompanies your self-signed certificate used by FlowForce.
openssl genrsa -out flowforce.key 2048
The private key must be in PEM (Privacy Enhanced Mail) format. The file extension of PEM files is usually .pem, but it can also be .key, .cert, .cer, or .crt. In order for the private key to be usable in FlowForce, it must not be password-protected. The private key must be stored securely.
2.Open the working openssl.cnf file and add the following section to it:
[ server_cert ]
# Extensions for server certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = server
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectAltName=DNS:server.my.domain.com
Make sure to change the subjectAltName (Subject Alternative Name) so that it corresponds to the FQDN (fully qualified domain name) of the machine where FlowForce Server runs. In this example, it is set to server.my.domain.com. Specifying a subject alternative name is required by Google Chrome 58 and later; otherwise, your self-signed certificate will generate a NET::ERR_CERT_COMMON_NAME_INVALID error (see the Chrome Help page).
3.Create a Certificate Signing Request (CSR), using the command shown below. Notice that the -config parameter points to the openssl.cnf file edited previously. The -extension parameter refers to the server_cert extension defined in openssl.cnf.
openssl req -config openssl.cnf -extensions server_cert -new -nodes -key flowforce.key -out flowforce.csr
4.When prompted, enter information about your organization, for example:
Country Name (2 letter code) [AU]: AT
State or Province Name (full name) [Some-State]: .
Locality Name (eg, city) []: Vienna
Organization Name (eg, company) [Internet Widgits Pty Ltd]: MyCompany Ltd
Organizational Unit Name (eg, section) []: IT
Common Name (eg, YOUR name) []: server.my.domain.com
Email Address []: test@example.org
For the Common Name field, make sure to enter the FQDN (fully qualified domain name) of the host machine where FlowForce Server runs. Leave the challenge password field empty when prompted.
5.Sign the FlowForce certificate with the root certificate. Note that, in a production environment, the root certificate does not normally sign server certificates directly; instead, intermediate certificates are used. The command below signs the flowforce.csr certificate request against the root certificate created previously and creates the flowforce.crt file (which is the server certificate required in FlowForce Server):
openssl x509 -extfile openssl.cnf -extensions server_cert -req -in flowforce.csr -CA root.pem -CAkey root.key -CAcreateserial -out flowforce.crt -days 365 -sha256
Summary
After taking Step 1 and Step 2, you must have the following certificates and keys:
•root.key: This is your certificate authority's (CA) private key. Store this file in a secure place; if this key becomes compromised, then anyone can generate browser-trusted certificates on your behalf.
•root.pem: This is the public certificate of your certificate authority. You will need to install (import) this certificate into the trusted certificates store of each machine (or browser) that needs to access FlowForce securely (Step 3 below).
•flowforce.key: This private key accompanies your self-signed certificate used by FlowForce (see next item).
•flowforce.crt: This is your self-signed certificate that will be used by FlowForce Server, FlowForce Web Server, or both.
Step 3: Import root certificate
When you create your own certificate authority (CA), the root certificate is self-signed; therefore, no browser will trust it by default. In order for an HTTP client (such as a browser) to trust your self-signed certificate, the certificate must be imported as follows:
•Into the operating system's trusted certificate store if the browser uses it. On Windows, for example, Google Chrome and Microsoft Edge use the operating system's certificate store, while Mozilla Firefox uses its own store. On Linux, Google Chrome and Mozilla Firefox use their own certificate stores (see next point). On Mac, Safari uses the operating system's certificate store (Keychain Access).
•Into the trusted certificates store of the browser itself.
Notes
•The self-signed certificate must be imported for each client machine (or browser, if applicable) that will access FlowForce Server. •When you enable SSL encryption between FlowForce Web Server and FlowForce Server, it is not sufficient to import the certificate into the browser. Your self-signed root CA certificate must also be trusted by the operating system.
|
Depending on your operating system, the instructions on how to import the root certificate vary. For details, see the subsections below.
On Linux, you can import a trusted certificate into the system's certificate store as shown below. Perform the following steps only if you are sure of the authenticity of the certificate you want to trust.
On Debian and Ubuntu, follow the steps below:
1.Copy the certificate file of the Web server to the following directory.
sudo cp /home/downloads/server_cert.crt /usr/local/share/ca-certificates/
2.Update the certificate store as follows:
sudo update-ca-certificates
On CentOS, follow the steps below:
1.Install the ca-certificates package:
yum install ca-certificates
2.Enable the dynamic certificate authority configuration feature:
update-ca-trust enable
3.Copy the server certificate to the following directory:
cp server_cert.crt /etc/pki/ca-trust/source/anchors/
4.Use the following command:
update-ca-trust extract
For cases in which you need to access the server only through the browser, it is sufficient to import the certificate into the browser certificate store. The exact instructions will vary for each browser. For example, in Firefox 59.0.2, you can do this as follows:
1.Under Options | Privacy & Security, click View Certificates. 2.On Authorities tab, click Import and browse for the root certificate file created previously. 3.When prompted, select Trust this CA to identify websites and click OK.
|
On macOS, you can import a trusted certificate into Keychain Access as follows:
1.Run Keychain Access. 2.Click System and then click Certificates. 3.Open the File menu and click Import Items. 4.Browse for the trusted certificate and click Open. 5.Enter the Keychain Access password when prompted and then click Modify Keychain. 6.Double-click the certificate, expand the Trust section, and select Always Trust. 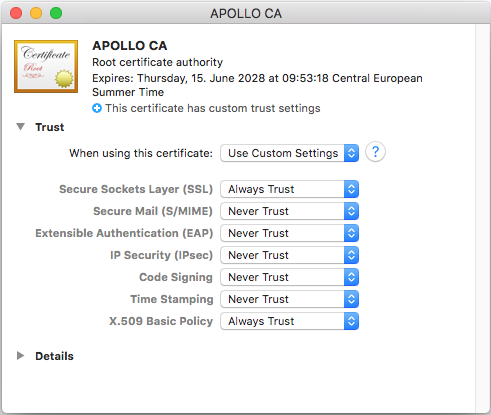
|
On Windows, you can manage certificates in the Microsoft Management Console (MMC) snap-in, either for your user account or for the computer account.
To open the Certificates snap-in for the current Windows user, run the following command in the command line:
certmgr.msc
To open the Certificates snap-in for the computer account, take the steps below:
1.Run mmc in the command line. 2.Go to the File menu of the MMC and click Add/Remove Snap-in. 3.Click Certificates and then click Add. 4.Select Computer account and click Next. 5.Select Local computer and then click Finish.
On Windows, you can import a trusted certificate into the system certificates store as follows:
1.Open the Windows certificate store for the computer account, see . 2.Expand the Trusted Root Certification Authorities folder of the Certificates (Local Computer) tree, right-click Certificates, select All Tasks | Import and follow the Certificate Import Wizard.
For more information, see the article Import a Certificate on the Microsoft website.
|
Next step
After taking Steps 1-3, you can now enable SSL for FlowForce Server, FlowForce Web Server, and for the HTTP connection between them, which is described in Step 7 of the section Set Up SSL Encryption.
